Chuỗi
BNB Beacon Chain
Lớp quản trị & stake của hệ sinh thái BNB Chain
Nhà phát triển
Hệ sinh thái
Staking
Earn BNB and rewards effortlessly
Tokenization Solutions
Get Your Business Into Web3
Cộng đồng
Beyond the Big Bang: Security and Risk Control Whitepaper v1.0

1. Introduction
Launched in September 2020, BSC currently bolsters an ecosystem of 800+ dApps, while delivering super-speed and record-breaking all-time-high (ATH) of 13.1M daily transactions. Being one of the largest Layer1 EVM-compatible blockchains, BSC also stands as the top performance blockchains to pilot new business innovations with its large ever-increasing user base and developer-friendly infrastructure. A wave of retail and new users have also supported the growth of BSC via NFTs, GameFi, and various other dApps.
At the time of record (August 10, 2021), DeFi has already locked more than $100 billion. This figure equates to more than a 1000% increase from the $10 billion at the start of 2021. BSC contributed 50B $ of TVL in the ATH days. The rise of hacks on BSC was accelerated through its popularity and the participation of new users in the BSC ecosystem. The USD value locked in BSC has grown exponentially, reaching more than $20 billion. This total has doubled in the past six months and touched an all-time high of $50 billion in May.
However, the explosive growth of BSC attracts not only the attention of new investors but also hackers.
The hacks and thefts have netted $839.4 million from DeFi, 0.8% of the total value locked in the past eight months. At $839.4 million, the amount netted from DeFi-related hacks already surpasses the $254.9 million stolen by hackers throughout 2020.
In Q1 2021, 75% of DeFi exploits are majorly on Ethereum. From Q2, both Total Value locked (TVL) and daily transactions on the BSC surpassed that on Ethereum, while BSC expands its footprint, hacks on DeFi protocols housed on the network increase hand in hand. In Q2, 57% of major DeFi exploits and frauds were related to the BSC. Polygon also sees an uptrend in DeFi-related hacks in Q2 as the rise of TVL. In Q3, after the BSC community took serious measures in security, DeFi-related hacks and frauds on BSC show a downward trend.
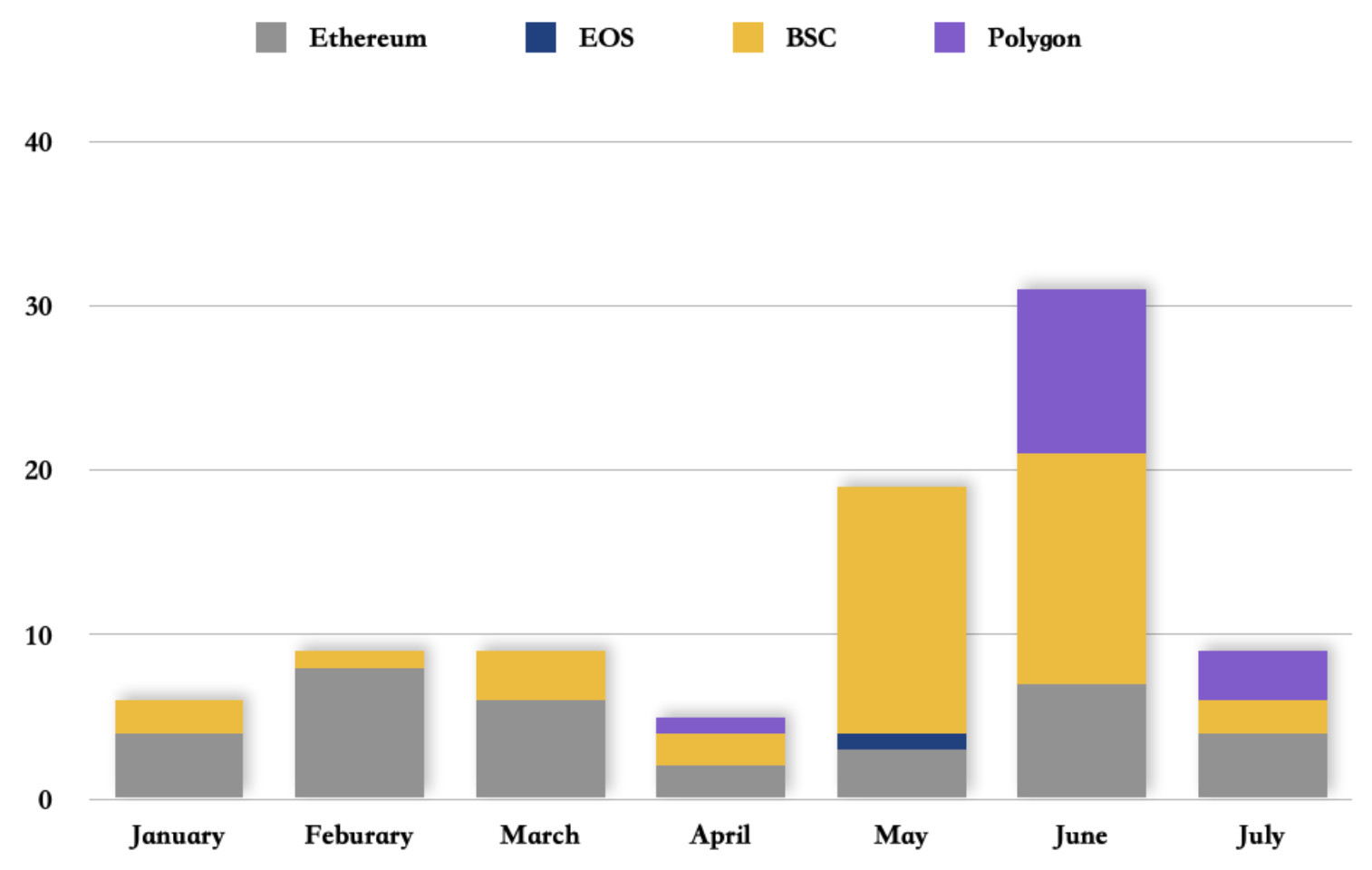
Regarding the attack techniques, we also found that Rug pulls have been on the rise since the early stage of blockchain development. Increasing volume attracts more malicious parties motivated by the increased incentives. This brought new challenges in the form of Logic errors and Flashloans.
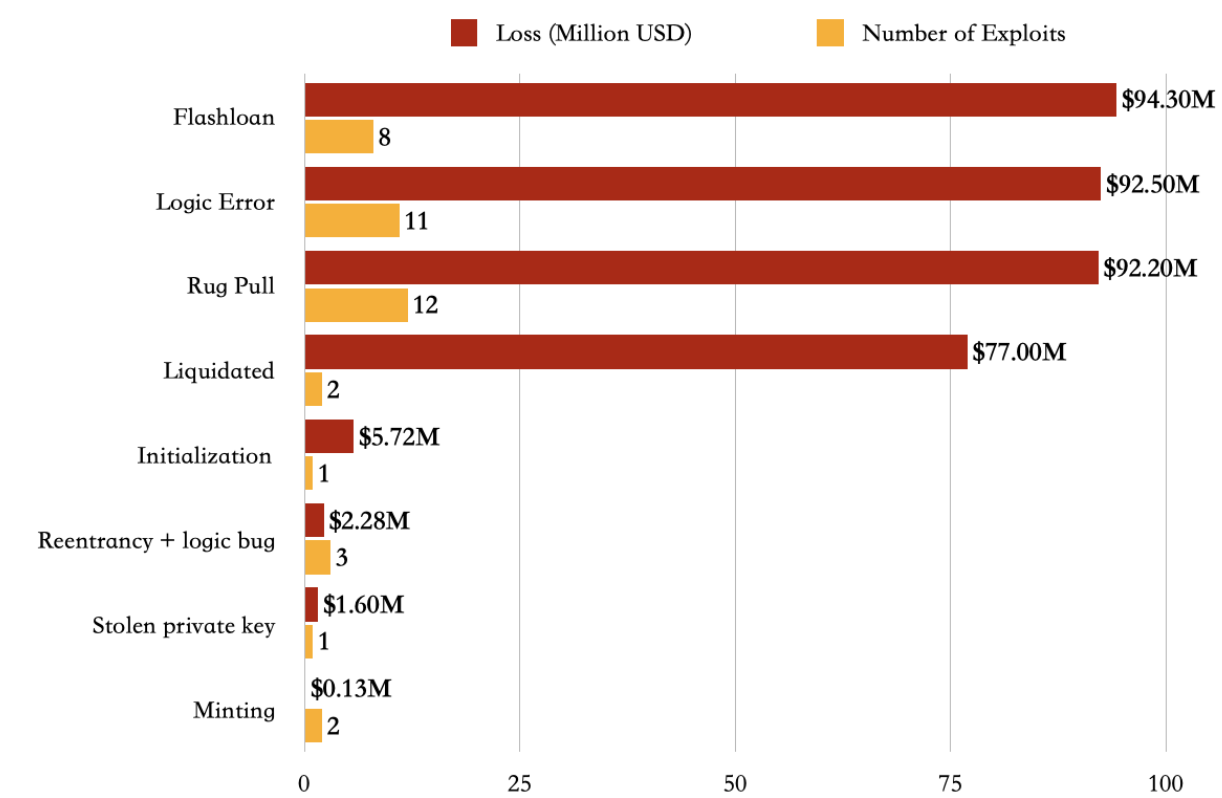
For example, nearly 66% of major fraud and misappropriations volume stemmed from DeFi protocols performing rug pulls in Q1 2021 on BSC; total, loss netted $94.3 million. After BSC’s TVL, liquidity, and daily transactions hit an all-time high, Logic error and Flash loan attacks dramatically increased in May.
In this paper, BSC’s Security Alliance (PeckShield, CertiK, Immunefi,Binance Security) will summarize the current security challenges and also highlight the new opportunities in the ecosystem. This will also include information around security audits, bounty programs, proactive monitoring, and cross-chain bridges.
TL;DR:
1. Security Audit: More than 300 projects went through professional security audits. However, as BSC projects are becoming increasingly complex, financial exploits are also getting more sophisticated. There are several key common patterns including:
- Though forks are common among BSC projects, many of these forks include significant changes to the original project’s codebase, which impacts logic and integrity
- Many projects do not follow proper key management and other trust-building security procedures for the community (i.e., admin/owner is not bound with timelock or multisig)
Some projects got exploited even after security audits. It is critical to continue monitoring projects after the audits are completed. Security incidents are increasingly happening due to post-audit issues like key leakage or EOA controlling admin.
2. Bounty Programs: The bug bounty platforms are now cultivating communities of whitehat hackers and security experts and driving them to review contract codes. Bug bounties are not well established in the BSC community. Projects did not understand how to set up and adequately run bug bounty programs yet. As of 2021 Aug, around 90 Ethereum projects have hosted bug bounties via the Immunefi bounty program, compared to 25 BSC projects.
Priority ONE - Joint bug bounties will introduce effective incentive structures for security talents to protect the BSC community. In addition, they also promote an understanding that proactively protecting BSC contracts through distributed and ongoing code reviews can be a viable career path for security researchers.
3. dApp Monitoring: Interactive attacks use stealthy or novel techniques to break the blockchain ecosystem. Hence, monitoring & alerting is vital when projects’ smart contracts go live, and now we see leading security firms like CertiK investing more resources in such areas to provide on-chain and off-chain insights and continue preventive scannings against known vulnerabilities and past security incidents.
It is important to follow a guarded launch approach and apply necessary risk control measures to monitor any abnormality in a real-time manner actively. As Similar incidents increase, keep an eye on DeFi security incidents, read the relevant post-mortem analysis and verify your project again to avoid similar attacks.
4. Cross-Chain Bridge: As DeFi is booming, cross-chain is indispensable. Several cross-chain products were launched in the BSC ecosystem. However, cross-chain security concerns also emerged. It either becomes an important tool to cash stolen assets out or a key target for attacks.
PeckShield suggests the automation of the alert process by providing a set of urgent APIs to access these exploit addresses. All the bridges could make use of these APIs to internally compute risk scores and may opt to take custom actions, e.g., temporarily pause or freeze pending human intervention to safeguard the BSC and minimize possible damages.
2. Security Auditing is a Continuous Process
A security audit is the most important requirement for every crypto project to secure its protocol and protect investor funds. Communities rely on audits to understand the security posture of a project’s smart contracts.
These days, most crypto projects receive an audit as a standard part of their development process. The explosive growth of the BSC ecosystem has led to high demand for audits, and in response, leading firms like Peckshield and CertiK have dedicated a significant amount of resources towards security audit efforts.
CertiK has audited more than 300 BSC ecosystem projects this year and has made those audits accessible through its community-facing security leaderboard at https://www.certik.org/boards/bsc. The audit reports provide end-users with an accessible source of information to understand the security risks associated with a project.
2.1 Challenges
As the crypto ecosystem grows, so will the number of hackers committed to finding new vulnerabilities in the smart contract codes. Decentralized Finance (DeFi) projects with millions of dollars in value locked continue to attract malicious actors looking for a way in. Constantly improving their exploit techniques, and we plan to stand miles ahead of them.
Many of the leading DeFi projects are experimenting with complex business logic that introduces new attack vectors previously not known or detectable. Investing in continual training and development is important for performing high-quality and trustworthy audits.
There are a few key challenges commonly found with BSC projects in particular:
- Business logic for BSC projects is becoming increasingly complex, and financial exploits are getting more sophisticated in ways that tactically bypass security checks.
- Most BSC project teams remain anonymous and are unwilling to make KYC compulsory, making it extremely difficult to get insights into non-audit-related identity information.
- Forks are extremely common among BSC projects, and many of these forks include significant changes to the original project’s codebase, which impacts the integrity.
- Centralization remains a top concern as nearly all projects have privileged controls over their protocols, and many are not as decentralized as they claim to be
- Many projects do not follow proper key management and other trust-building security procedures for the community (i.e., admin/owner is not bound with timelock or multi-sig)
2.2 Opportunities
There have been many lessons learned and also new opportunities in security audits:
- Audits are a necessity, not an option. Investors rely heavily on audits for insights. Audit plays a significant role in helping investors make more informed decisions. Security firms need to dedicate more resources to enhance the overall quality of the security audits and make them accessible to all.
- Security software and tooling are essential to enhance the audit process. Security audits are by their nature human-intensive processes, and issues are inevitably missed from time to time. Building more audit software and tools, e.g., scanning a similar vulnerability, identifying the private key management issue, can improve the overall audit quality and reduce misses.
- It is critical to continue monitoring projects after the audits are completed. It is common practice for firms not to keep monitoring projects once the audit is complete. Security incidents are increasingly happening due to post-audit issues like key leakage or EOA controlling admin. Security companies like Peckshield and CertiK are dedicating more resources for project monitoring and alerting, as well as building a threat zone to collect first-hand information (in Section 4)
3. Bug Bounty Programs
Bug bounty platforms are now cultivating communities of whitehat hackers and security experts, driving them to review contract code. As soon as a vulnerability is discovered, bug bounty platforms facilitate responsible disclosure of those vulnerabilities directly to the projects.
Today, bug bounty programs are an ongoing security measure not yet well-established in the BSC community, but all projects need to set up and properly run these programs. It is extremely difficult to understand and fix the types of vulnerabilities that might arise in smart contract development without bug bounties. All projects must leverage BSC's tools and support to learn how to attract and engage hackers to review their live smart contract code.
As of 2021 Aug, ~90 Ethereum projects have hosted bug bounties on the bug bounty platform Immunefi, compared to 25 BSC projects.
3.1 Challenges
Before the rise of BSC bug bounties, there was neither a large smart contract security community on BSC nor effective incentives to engage in crowdsourced code review and responsible disclosure.
Not only will the rise of bounty programs in BSC mean that researchers will be able to make a career out of bug hunting, but it will also result in the creation of new security standards. However, there remain several challenges, from both bounty processes to incentive models.
- The bug bounty process must become more steady, reliable, and predictable, so that hackers can devote their best attention to protecting BSC projects, knowing they will be well-compensated. While bug bounty programs are proving their effectiveness, they remain volatile experiences for security professionals and whitehat hackers, and this volatility must be eliminated.
- The other important element of these standards shifts is that of incentive models. The few projects that managed to run bug bounties independently often faced significant difficulties in rationally pricing vulnerabilities according to their actual market value. As a result, low bug bounty payouts resulted in a dearth of security talent reviewing the code, leading to a meager bug submission rate and a far more fragile BSC ecosystem.
3.2 Opportunities
Many of these problems can be eventually resolved by the scaling bug bounty, the standard that vulnerabilities should be dynamically priced according to potential economic damage. This model drove the creation of the world’s largest bug bounties since potential economic damage in smart contracts with hundreds of millions or even billions in funds is much more straightforward than in other industries. Consequently, with incentives to disclose vulnerabilities skyrocketing, the amount of security talent working to protect the community has skyrocketed.
As a result of the work of bug bounty platforms like Immunefi, the BSC community will have a comprehensive and structured understanding of what types of vulnerabilities projects are likely to face (logic errors, flash loan attacks, sandwich attacks, etc.) and how they should be ranked in terms of severity. It has expectations about where disclosures should happen and how. This makes it far easier for the security community to pitch in because there are clear expectations on work and rewards set for all.
To maximize the spread of these new security standards, BSC Accelerator Funds has created a new crypto-specific security standard: Priority ONE - Joint bug bounty program. Under a joint bug bounty program, an ecosystem or community of projects will pool resources to match bug bounty payouts of projects in that ecosystem. In doing so, the standard of security is markedly increased across the entire ecosystem, meaning that capital can more safely flow between protocols. Priority ONE, backed by 30,000 BNB (over $10mm today), is one of the most ambitious of these programs. If similar programs are anything to go by, it will likely save tens--if not hundreds--of millions of dollars by driving vulnerability disclosures, thereby preventing malicious hacks.
4. From Reactive to Proactive dApp Monitoring
DApp monitoring is a vital part of alerting the community when the potential risk occurs. DApp monitoring can help alert related communities, manage their risks, and minimize damage when done right.
Advanced tools will also play a growing role in strengthening the quality of audits and enhancing a project’s overall security protection.
4.1 Current State
CertiK has built in-house audit tools that leverage their growing database of known vulnerabilities compiled based on thousands of audits performed. Skynet, a 24/7 real-time monitoring software to protect against security incidents after a smart contract is deployed.
CertiK’s Security Leaderboard is the leading security-focused ranking platform where users can analyze the security status of blockchain protocols and DeFi projects. The Leaderboard includes an exclusive section for BSC projects at certik.org/boards/bsc, which provides the BSC community members and builders with a powerful platform to conduct their security research.
The goal of the Leaderboard was simple: to make professional security audits accessible to the crypto community so users can understand the risks of projects before investing or interacting with their smart contracts. Prior to the launch of the Leaderboard, projects needed to share their audit reports through several different platforms, like GitHub and Telegram, which also required the project to prove the authenticity of the audit itself. The launch of the Security Leaderboard addressed these critical pain points and provided a one-stop-shop for the end users’ security needs.
A key enabler of the Leaderboard is CertiK’s Skynet - an intelligence engine that offers real-time security insights on blockchain and smart contract projects. Skynet ingests data from several different sources and presents the information as an easy-to-digest security score that summarizes a project's overall security status. The insights generated by Skynet are integrated into Security Leaderboard profiles and offer transparent and easy-to-understand security information to the public. Skynet also acts as a notification system that provides clients with real-time alerts when they detect abnormalities and suspicious activities.
Skynet is one of CertiK’s latest offerings to enable a more secure BSC community through real-time insights and trusted security intelligence. Since its launch earlier this year, more than 100 BSC projects have implemented Skynet to receive 24/7 security monitoring and alerts, along with much more insightful information provided to end-users on the real-time security posture of their protocol.
CertiK designed Skynet using advanced tools and industry-leading methodologies. Skynet runs 24/7 to offer protection after a contract is deployed on the blockchain network, collecting and analyzing large amounts of on-chain and off-chain data. Skynet analyzes the continuous data ingestion via a range of machine learning and data science tools using security-centric algorithms designed by the CertiK team. This complex analysis ultimately leads to a simplified metric, known as the security score, which indicates the security level of a corresponding project from a score of 0 to 100.
Six security primitives that contribute to the calculation of a project’s security score:
- Static Analysis: Source-code/bytecode scanning via CertiK’s proprietary static analysis tools.
- Social Sentiment: Analyzing social growth, geographical clustering, and other sentiment variables from social data feed.
- On-Chain Monitoring: Utilizing real-time security monitoring of on-chain contracts and activity through intelligence systems.
- Governance & Autonomy: Monitoring and tracing tool for sensitive contract roles or key addresses.
- Market Volatility: Measuring an assets’ financial factors and market metrics.
- Safety Assessment: Leveraging fact-based and multi-faceted proprietary safety evaluations.
As BSC’s trusted security partner, CertiK’s mission is to produce trustworthy security insights for the community. CertiK’s growing team of security researchers have built Skynet and the Security Leaderboard to create a foundation to help BUIDL secure projects, be SAFU, and provide a more robust backbone to support a flourishing BSC ecosystem.
4.2 Opportunities
4.2.1 Proactive Scanning
Skynet Scanning is highly effective at quickly detecting security vulnerabilities in a project’s off-chain status and on-chain contracts. It is mainly designed and implemented to monitor blockchains and smart contracts in real-time once they are deployed, helping to address a major pain point with crypto around dynamic security analysis. The Skynet framework allows for static analysis, fuzz testing, formal verification methods for pre-defined security specifications, along with other tested monitoring techniques. While audits are highly effective in catching critical issues before launch, Skynet offers real-time security vulnerability analysis and security evaluation of the smart contract once it’s live in the network.
Skynet Scanning is one of the new analysis components that was recently launched and is designed to reveal particular types of semantic vulnerabilities. The semantic vulnerabilities refer to the non-codebase flaws, which cannot be alarmed by the traditional software testing tools. The general workflow of Skynet Scanning is displayed below: Skynet Scanning consists of 4 main components: Hack Knowledgebase, Kinship Scanner, Rugpull Scanner, and Dependence Scanner.
Hack Knowledgebase
Recently, with the increasing number of attack vectors and concrete vulnerabilities, the accumulation of domain knowledge ensures broad coverage against hacks. Hack Knowledgebase is one of CertiK’s tools intended to lower the burden of domain knowledge accumulation and expand knowledge sharing among professional auditing experts.
Hack Knowledgebase contains a growing database of hack event details in various formats, such as scripts triggering the hack events. These scripts will automatically scan any given smart contract and detect if the exact attack vector is present in the code. Each hack event detail can be well defined and stored in a distributed structure. In this case, an attack vector that consists of multiple different attack methods can still identify in a self-heuristic manner through these scripts containing the hacking knowledge.
Kinship Scanner
Kinship Scanner utilizes accumulated domain knowledge and reveals the semantic relations between smart contract projects. Built upon CertiK’s in-house kinship algorithm, the relations that are among any given project in the hack knowledgebase can be accurately revealed on function, contract, project levels.
The Kinship Scanner, along with the Hacking Knowledgebase, bring the following enhancements to the Skynet:
- Forward Vulnerability Scanning: Given a new project, its “relatives” vulnerabilities will automatically reveal. The feature is helpful for forks-type projects.
- Backward Vulnerability Scan: Any new project’s known vulnerabilities will be used as a sample to detect all the previous projects. Given a known vulnerability, all of the project’s “relatives” will be scanned, and vulnerabilities and these “relatives” will be alerted.
Rugpull Scanner
Rugpull Scanner is the new effort to connect formal verification techniques and practical semantic vulnerability analysis in a scalable manner. For example, given a smart contract, the risk of a rug pull is defined by the severity of the ownership centralization, including the number of owner-controlled functions and their complexity. The contract’s owners can arbitrarily decide executions of significant operations (i.e., mint/burn token) regardless of a community's decisions. This risk will be evaluated by the rug pull scanner based on an in-house evaluation matrix. As an output, the diagrams of ownership can be generated to reveal the implicit rug pull potential automatically.
Dependence Scanner
One common concern from the crypto community is whether the audited codebase matches with the deployed contracts. This is because numerous deployments of the smart contracts are not specification consistent with their audited codebase, and there are many vulnerabilities introduced by on-chain operations on deployments (e.g., whether there are unverified third-party dependencies in the deployment). To monitor the safety of such on-chain deployment context, the Dependence Scanner is implemented and will send an alarm to the project team and community if there’s any on-chain update that may violate the pre-defined safety policy.
4.2.2 Proactive dApp Monitoring
Built on the earlier efforts in analyzing DeFi protocols in the past year, PeckShield also has developed an automated system to monitor and analyze BSC DApps.
DApp Monitoring covers a broad spectrum of monitoring, holistic threat intelligence, blacklist labeling and synchronization, and joint community feedback:
- Slippage Monitoring: real-time detection and notification of significant slippage changes.
- TVL Monitoring: hourly-based real-time monitoring and notification on sudden changes of TVLs.
- Monitor and report any unusual large transfer on BSC.
- Monitor and record any movement associated with blacklisted accounts (e.g., scams, frauds, rug pulls, phishing.
- Report scams or suspicious projects through the scam report channels: https://forms.coinholmes.com
dApp Monitoring is highly efficient at quickly detecting security possible scams, phishing, rug pulls, and hacks.
It is mainly designed to visualize ongoing hacks and unusual activities in hourly-based real-time, e.g., sudden changes of slippage and TVLS, large transfers, and blacklist. While audits are a basic safeguard in catching critical issues before launching, It is necessary to apply necessary risk control measures to actively monitor any abnormality in a real-time manner.
Slippage Monitoring
Many of the attacks against DeFi projects are designed to exploit slippage, which allows an attacker to extract more value than they put in based upon inaccurate exchange rates.
For example, The attack against Spartan protocol took advantage of a failure in the contract’s liquidity share calculation. The attacker inflated the asset balance within the liquidity pool, and burning pool tokens allowed them to withdraw an unfair share of the underlying assets.
To monitor the sudden slippage changes,, the threat Intelligence is implemented and will alert the deployers and community and prompt our emergency response procedure.
TVL Monitoring
A sudden change of TVL makes it possible to reason out about scenarios where the issue happens due to a change in something internal to the smart contracts.
For example, imBTC Uniswap Pool, Despite the fact that Uniswap does not support ERC-777 tokens, an imBTC Uniswap pool worth roughly 300,000 USD was drained using the reentrancy attack.
Identifying and exploiting attack vectors that exploit protocols’ interconnectedness, where the composability risks therein are often under-examined. In practice, a sudden change of TVL is detected and sends an alarm to the project team and community with further follow-up.
Blacklist Labeling
With the increasing number of rug pulls and hacks, Automatically keeping track of any movement of the blacklisted account is helpful for centralized institutions to react to the illicit flow of funds, identify suspects and track out the internal relation between several incidents.
Community Feedback
PeckShield shares any collected community feedback back to the Binance Security team with necessary follow-up efforts in better understanding the nature of possible scams, phishing, rug pulls, and hacks, as well as tracking the illicit asset flows and performing associated forensics. Once an account is added to our internal blacklist database, our system will then automatically keep track of any movement of the blacklisted account.
Emergency Response
After detecting any abnormal transaction pattern with an in-house real-time anomaly detection engine, the security response team would look into the protocol, analyze the root cause, give feasible suggestions, add into our blacklist database and keep track of any movement of the blacklisted account, and elaborate the technical details with possible write-ups in English and Chinese.
PeckShield's internal security response team would identify other potentially vulnerable DeFi projects with the same security issue, report to the deployed team with necessary follow-up efforts in raising necessary alerts to the affected community after handling an incident.
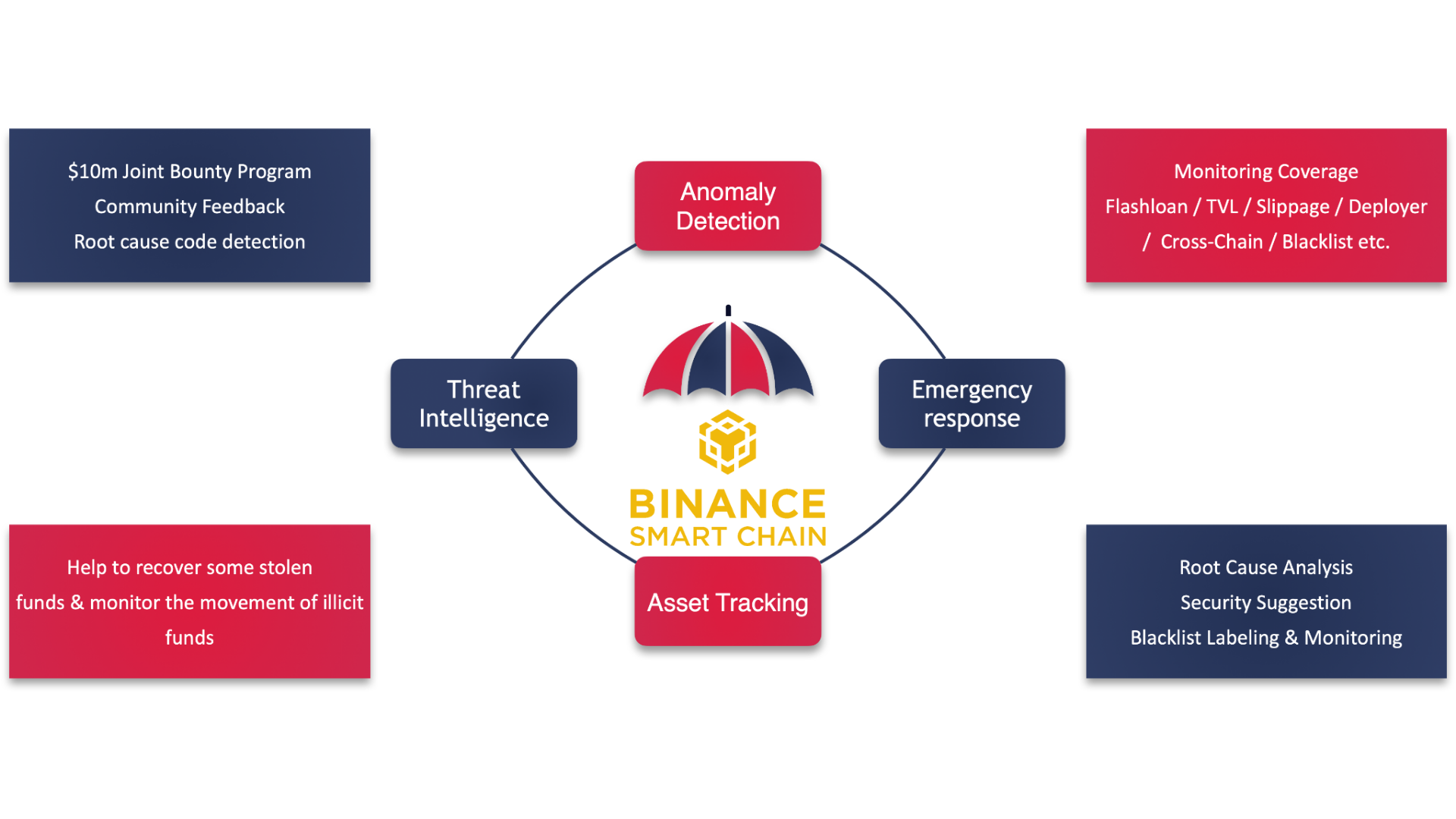
5. Trustless Cross-Chain Bridges: Build a Trustworthy Ecosystem
Cross-chain bridges are one of the most important critical infrastructures that empower the internet of blockchains and ensure a smooth exchange of liquidity between different chains. The BSC ecosystem has 10+ such cross-chain bridges that fuel the trustless ecosystem with trust. With more and more assets being bridged through these decentralized trustless bridges the more they prove to become the top channels for even the hackers to move the exploited assets out of the BSC ecosystem. This has led to a few challenges which can be tackled with coordination and security measures if implied for good throughout the ecosystem.
5.1 Challenges
Like most criminals, the exploiters also have patterns that include leveraging cross-chain bridges to transfer stolen gains to Ethereum, and withdrawing via Tornado Cash, an Ethereum mixer allowing users to withdraw funds anonymously.
PeckShield found that 55% of illicit assets (~$147 million) has been cashed out through cross-chain bridges this year (as of the end of June).
For instance, on May 1st, the Spartan protocol contract was exploited and incurred a $30 million loss. The attacker used the 1inch Exchange to swap all tokens to anyETH, and leveraged cross-chain bridges to transfer illicit gains to Ethereum.
Cross-chain bridges have become a key tool for attackers, as noticed at the beginning of Q3 2021. Losses from hacks in cross-chain bridges have hit an all-time high of $644 million, including Ethereum-Polygon-BSC based Poly Network’s loss of $611 million.
So far, these cross-chain bridge hacks add up to 28.6% of the major hacks in Q3.
On August 10th, More than $611 million was stolen from Poly network in what is likely to be one of the biggest cryptocurrency thefts ever. Fortunately, hackers have returned nearly all the funds they stole.
Poly Network is neither a crypto exchange nor a digital wallet platform. Instead, it helps facilitate crypto transfers between different cryptocurrencies’ blockchains. This can help people use their cryptocurrency across different networks.
5.2 Opportunities
PeckShield forecasts that the attacking and transacting criminal funds through cross-chain bridges are likely to grow. To prevent this, the best viable option is to freeze the funds sent to these cross-chain bridges. However, this risks the decentralization of ecosystems and is somewhat controversial in DeFi.
PeckShield suggests forming a joint effort alliance between the cross-chain bridges and all community members. It is imperative to keep tracking all movements of the blacklisted addresses and update the blacklist database in real-time. In the meantime, Binance Bridge, AnySwap, and Redbridge can help to temporarily pause or even freeze suspicious assets movement to minimize the damage better until more members are added to the alliance.
6. Conclusion
The BSC community has introduced holistic security infrastructures and services from security audits, bounty programs, and dApps monitoring in less than one year. It is an outstanding achievement, but far less than enough. In the paper, several key areas like proactive monitoring and trustless bridging are suggested as critical next steps to keep improving the maturity level of the BSC community. With Binance Smart Chain, security must be the top priority.
This whitepaper can play as a starting point to work closely with other blockchains, security experts, and more security companies and see how we can stop the potential hacks/exploits together in the decentralized world. As BSC is an EVM-compatible blockchain, the security challenges or issues in BSC will not be unique, and it may happen in other blockchains when their user bases are the same as BSC (hopefully not). We want to collaborate with other blockchains to resolve the common challenges and move the industry forward as one group with a shared vision.
If you have any suggestions or comments on this white paper, please feel free to contact us : BUIDL@binance.org